Think about your actions.
Is this safe?
What data or information am I giving away?
Is this an IT approved solution?







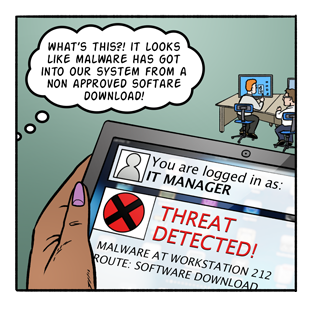

What is Shadow IT? It is now easier than ever for employees within an organisation to use and install, applications and Software as a Service (SaaS), without consulting their internal IT department. In addition, as the use of mobile devices within the workplace has become commonplace, employees expect to be able to use applications they use at home into their working lives. This is happening today, and is called ‘Shadow IT’ - it’s not a new phenomenon, but is a growing concern for organisations today.
Why? This rise in ‘Shadow IT’ is often driven by a desire for increased productivity and efficiency, but can have huge implications for organisations as it brings increased risk, security and compliance issues. By using ‘non-approved solutions’ it increases the chance of systems being attacked by cyber threats or loss of data. This is a risk, but by managing Shadow IT correctly it can be viewed as a powerful business enabler.
You may be already using a non-approved solution – it works great, but are you aware of the risks of your actions and what does that mean? Work with your IT department and talk through the options – what can you use and why, is the risk worth it? By working together these ‘Shadow IT projects’ can be supported and managed making sure the organisation stays safe and work is not affected.
How to make Shadow IT work for you, three actions that could help:Is this safe?
What data or information am I giving away?
Is this an IT approved solution?
Find out what's available to you.
Understand the risks and how they can be managed, understand their issues and focus on activities and issues that have the biggest impact to the business. Don't be afraid to make suggestions on new technology that could work for you.